Every year, many organizations decide to shift some computing operations to the cloud—frequently seeking flexibility and scalability, reliability, enhanced collaboration abilities, potential cost savings, and more. Cloud computing can also serve as an effective onramp for businesses to modernize and begin integrating technologies like data analytics and AI. While cloud service providers (CSPs) work to simplify the cloud migration and administration process, potential cloud adopters may not understand all that a CSP has to offer in vital areas like security. In a recent in-depth research paper, we explored how two of the world’s largest technology companies—Microsoft and Red Hat—partner to provide customers with multiple layers of cloud-native security.
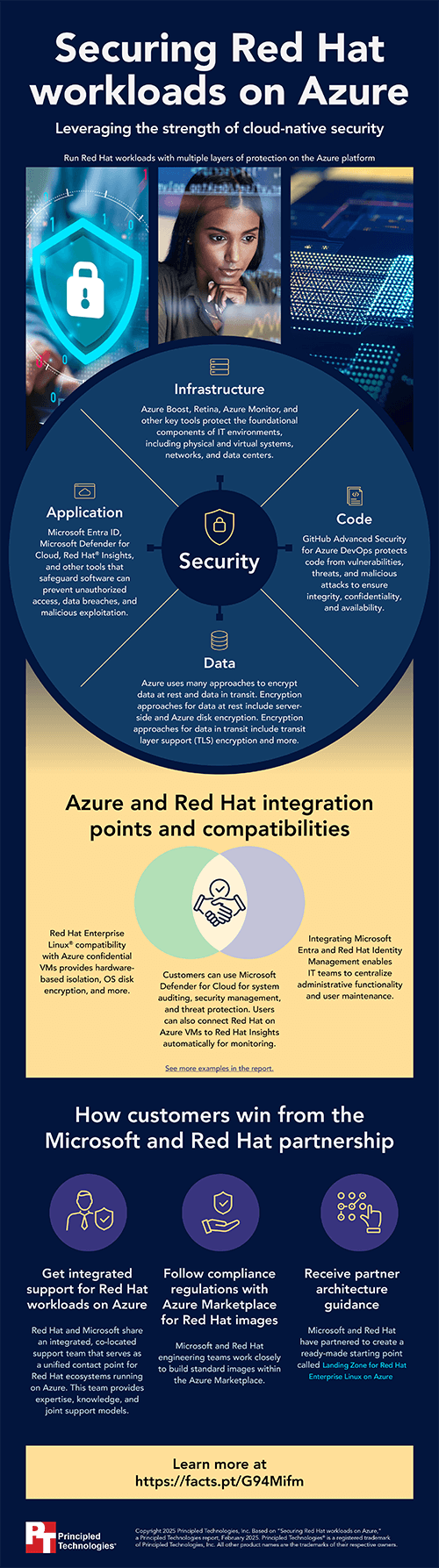
In the course of our research, we reviewed extensive, publicly available documentation and conducted direct interviews with Microsoft and Red Hat subject matter experts. We investigated the security features that each platform offers and outlined how they intersect to provide enhanced, multi-layer protection for Red Hat on Azure deployments. We focused on four primary types of security—infrastructure, application, data, and code—and then dove into the details of the security tools that administrators working in Red Hat on Azure ecosystems can access in each case.
We found several areas where the collaboration between Microsoft Azure—with its extensive service portfolio and integration capabilities—and Red Hat—with its enterprise-grade open-source solutions—can help organizations protect their data and meet evolving cloud security needs. In addition to the expansive technical feature set available with both platforms, users can benefit from a cooperative approach that's produced co-engineering initiatives, ecosystem integration, and partner guidance on architecture and design. With Red Hat on Azure solutions, administrators have access to a broad and deep set of security features and applications that can help them protect their vital data assets.
To learn more about the security features available while running Red Hat workloads on Azure, check out the report, infographic, and summary presentation below.
Principled Technologies is more than a name: Those two words power all we do. Our principles are our north star, determining the way we work with you, treat our staff, and run our business. And in every area, technologies drive our business, inspire us to innovate, and remind us that new approaches are always possible.